I recommend you to follow the Terminal Setup before using TShark1.
Why use TShark
TShark bring easy and fast statistics. TShark is a terminal oriented version of Wireshark designed for capturing and displaying packets when an interactive user interface isn’t necessary or available.2
Packet Analysis
Throughout this guide I will be using a pcap3 from malware-traffic-analysis.net
following Structured Analysis
File/Stream reading
Options:
-i <interface>, interface <interface>
-D, --list-interfaces print list of interfaces and exit
-r <infile>, --read-file <infile> set the filename to read from (or '-' for stdin)
-c <packet count> stop after n packets (default: infinite)Stream
List interfaces by using the command tshark --list-interfaces
sudo permission is usually required to select hardware interfaces.
tshark --interface eth0File
tshark --read-file 2022-03-21-traffic-analysis-exercise.pcapStatistics
4 To view the available statistics use the following command: tshark -z help. Example
Options:
-z <statistics> Use the -q option if you’re reading a capture file and only want the statistics printed, not any per-packet information.
-z help Display all possible values for -z.
-z io,phs Create Protocol Hierarchy Statistics listing both number of packets and bytes.
-z io,stat,<interval> Collect packet/bytes statistics for the capture in intervals of interval seconds.
-z endpoints,<type> Create a table that lists all endpoints that could be seen in the capture.
-z conv,<type> Create a table that lists all conversations that could be seen in the capture.
-z http,stat Count the HTTP response status codes and the HTTP request methods.
-z http_req,tree Calculate the HTTP requests by server. Displayed values are the server name and the URI path.
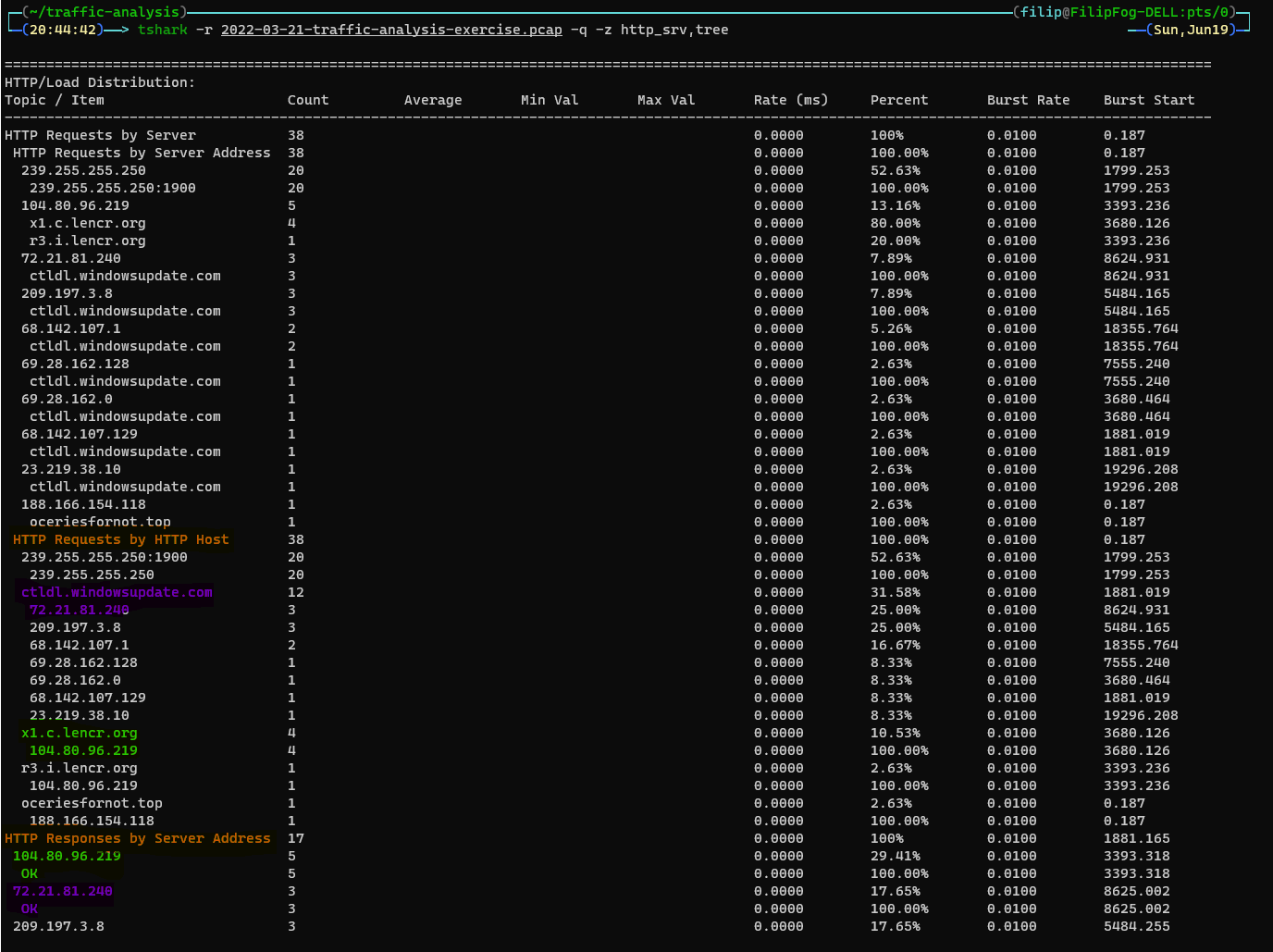
-z http_srv,tree Calculate the HTTP requests and responses by server.
-z credentials Collect credentials (username/passwords) from packets. Currently implemented protocols include FTP, HTTP, IMAP, POP, and SMTP.Protocol Hierarchy & General Statistics
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z io,phs
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z io,stat,600Example: Protocol Hierarchy | Example: Bytes statistic
Endpoints
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z endpoints,ip
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z endpoints,tcp | lessExample: IP Endpoints | Example: TCP Endpoints
Conversations
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z conv,eth
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z conv,ip
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z conv,tcpExample: eth | Example: ip | Example: tcp
HTTP
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z http,stat
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z http_req,tree
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z http_srv,treeExample: HTTP Stat | Example: HTTP Requests | Example: HTTP Response
Credentials
tshark -r 2022-03-21-traffic-analysis-exercise.pcap -q -z credentialsFiltering
https://www.tcpdump.org/manpages/pcap-filter.7.html
Export Objects
Options:
--export-objects <protocol>,<destdir>
Export all objects within a protocol into directory destdir.
The available values for protocol can be listed with --export-objects help.