The Sliding Scale
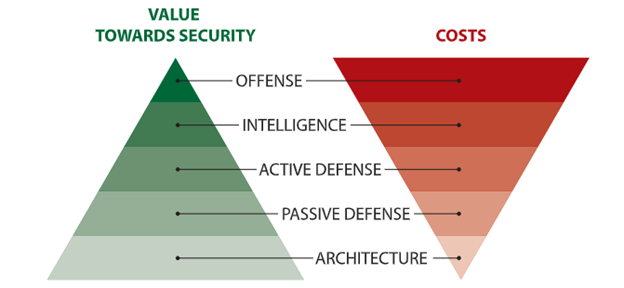
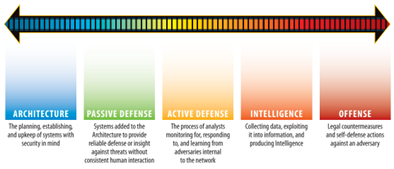
We always have to prioritize our choices, which will lead us to our goal, and that is hard. There are many vendors out there that wish to sell us solutions that have the same goal as ours: improved security. But we don’t have the resources to choose all of them. A model to use for prioritization is: “The Sliding scale of Cyber Security”1, by Robert M. Lee. This model shows us five seucirity categories in order:
- Architecture
- Passive Defense
- Active Defense
- Intelligence
- Offense
A Good Foundation
Cyber security must be built with a good foundation. If a house is not built with a good foundation, it will fall. We need to follow a layered approach regarding security, regardless of profession. A layered approch is about adding multiple preventive measures to prevent or minimize damage. This principle does not only exist in the IT world but also in other professions: health2, law3, construction4, etc.
Building a good foundation takes time, energy, and resources. It has to be planned, designed, and constructed. You also have to maintain it. The foundation, or in other words the architecture should be built with the needs and requirements in mind. If the needs and requirements changes, you may have to rebuild the architecture. And there are no silver bullet or architecture that fits everyone. But a good architecture is always accompanied by good design drawings. The architecture was designed to meet the expectations that would be put on it, and it followed good guidelines.5 After designing the architecture, we can then start to buy the “Iron” that is going to be used in our foundation.6 After our foundation is casted, we can start adding preventive measures.
Preventive Measures
Preventive measures are usually inside the passive defense category. Excellent preventive measures are systems or solutions that is added to the architecture to deliver constant defense without human interaction.
Some preventive measures do not fall inside passive defensive but rather active defense. Examples of these preventive measures are: monitoring, response, and continous assesment. These measures requires a lot more resources to be of use. And they don’t give the same amount of security, related to the amount effort put in, as the other preventive measures in the passive defense category. Nevertheless, they are of high importance since they are used to know the state of the construction. Everyone buys a fire alarm, security cams, or a service from a monitoring center, because we care about our house and wants to protect ourselves. Even so, in the IT world we forget about the process behind responding to those alarms. What action do we take when we recieve a call that tells us that there are suspicious activity comming from our network? We need to create procedures and routines for these things. Monitoring is useless without the response.
There are some areas you have full responsibility over, and you have no opportunity to outsource it. (Even if you can, you shouldn’t.) But there are other areas of responsibility you can outsource, or set aside to someone else. It is recommended to outsource those areas, if you are a small business with limited resources, because it requires expertise and resources to execute. Find a security partner which delivers services that makes your security holistic.